Hello! I’m Tareq from Knight Squad.
Recently Inter-University Cyber Drill 2021 was held & total 287 teams participated. Challenges were sorted by challenge category.
- Basic
- Cryptography
- Forensics
- ICS Problem
- Incident Handling
- Reverse Engineering
- Web Vulnerability
Here I’m going to give you a quick writeup for the challenges that I was able to solve. I will provided all the links according to the challenges. Hope you guys will find this helpful. You will find all the challenges here : http://20.39.34.98/CyberDrill/ [ A Special Thanks to Abrar Mostafiz YEALID brother ]. You will find the scoreboard here : http://cyberdrill.cirt.gov.bd:3000/scoreboard
Basic:
This category contains some basics of CTFs.
Prerequisite: the basics of CTFs.
Cyber security TRIAD : [ 50 ]
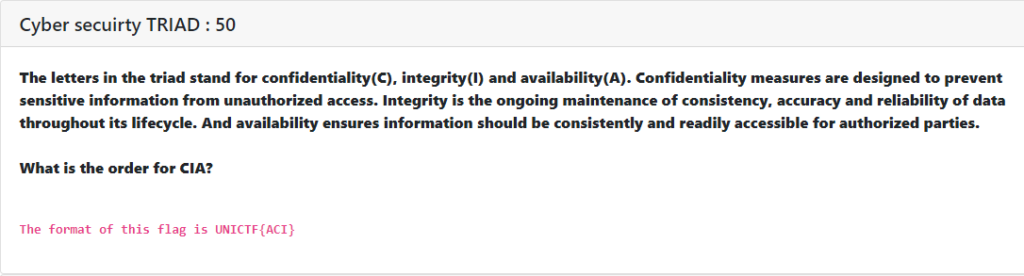
This was a very basic challenge with some basic cyber security information. Here we had to find the order of CIA. The word CIA contains 3 letters. If we arrange the letter one by one we get 6 combinations.
CIA
CAI
ACI
AIC
IAC
ICA
The correct order was IAC. So the flag was UNICTF{IAC}
Sometime common things are mistaken!: [ 50 ]
In the challenge we were provided with a egg.png file which contained a QR code.

So I just scanned the QR code online & got a link. After visiting that link I got another GitHub link.
On GitHub there was a simple python code. I thought I have to run the code & it will give me the flag. But I was wrong.
Then I checked the history of that repository & found 2 files. One was “Create find_me-uni-ctf2021” & the another was “Update find_me-uni-ctf2021”. So I browsed to “Update find_me-uni-ctf2021” & got the flag.
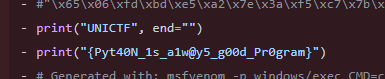
An Eagles eye shot! : [ 100 ]
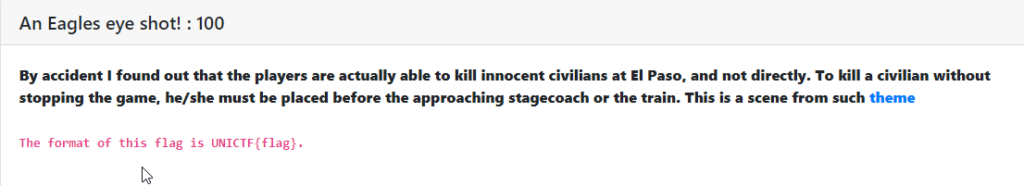
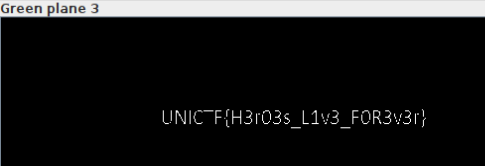
In this challenge we were provided with a hawkeye.png file. There was a hint on the challenge description [ “stagecoach” ]. I ran strings & grep, exiftool, binwalk, foremost, zsteg but nothing worked for me. Then I used stegsolver.jar & changed the color panel. After changing some panel I got the flag.
You will find stegsolve.jar here.
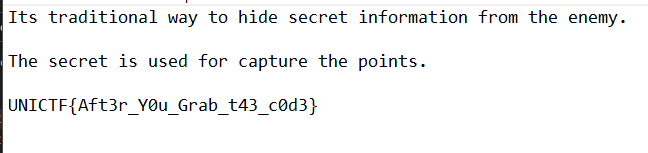
Secrecy is nothing! : [ 200 ]
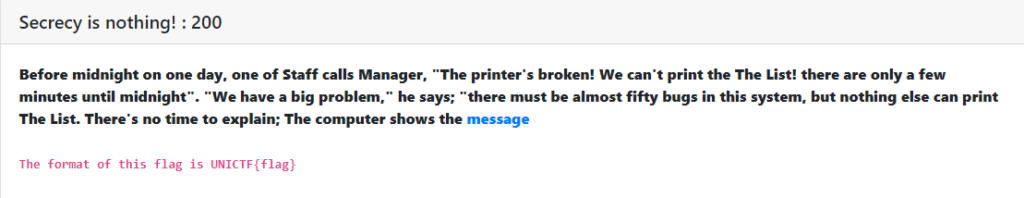
In this challenge we were provided with a link. The link contained something like this.

If we visit the source code & zoom out we can see a picture like this.

In the picture we can see a girl standing. The picture was a ascii image art. Google it you will find more details. So I browsed to a ascii image art decoder. [ https://pictureworthsthousandwords.appspot.com/ ] & got the flag.
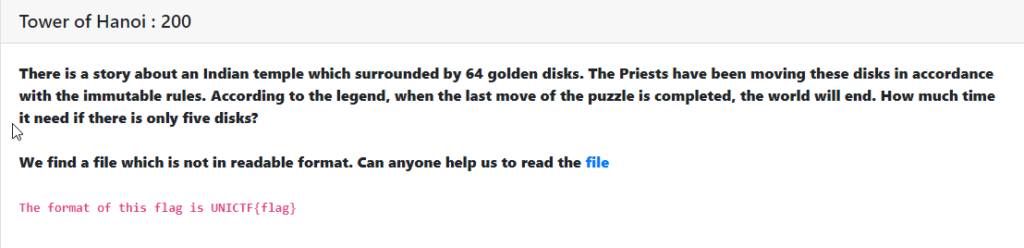
Tower of Hanoi : [ 200 ]
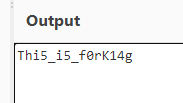
In this challenge we are provided with a file which contained a very long base64 data. I just decoded it from base64 31 times & got the flag.
Cryptography:
This category is based on Cryptography. you can easily solve these challenges. These challenges were really easy compared to other CTF Competitions.
Prerequisite: knowledge of Cryptography & CTFs.
Crypto 000 : [ 25 ]
In this challenge we were provided with a encrypted message which we have to decrypt. The message was encrypted with Alphabetical Subtraction. I just decrypted it & got the flag.
Crypto 001 : [ 25 ]
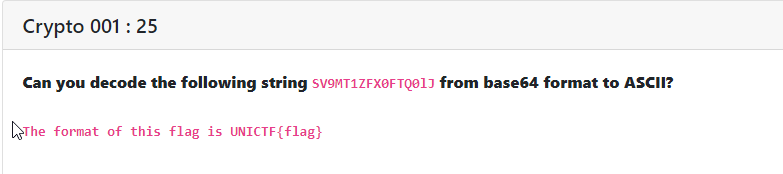
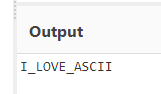
This challenge really a very easy challenge. We just have to decode the base64 to plain text.
Crypto 002 : [ 50 ]
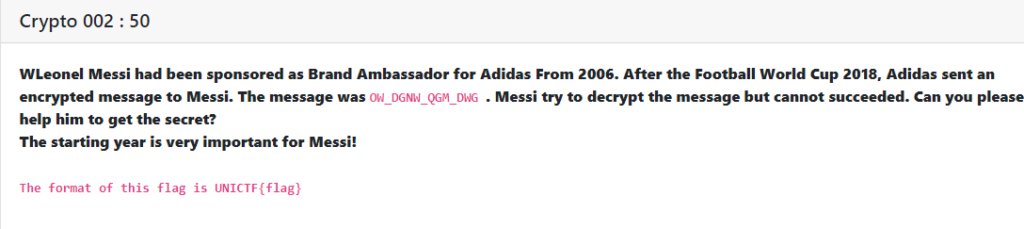
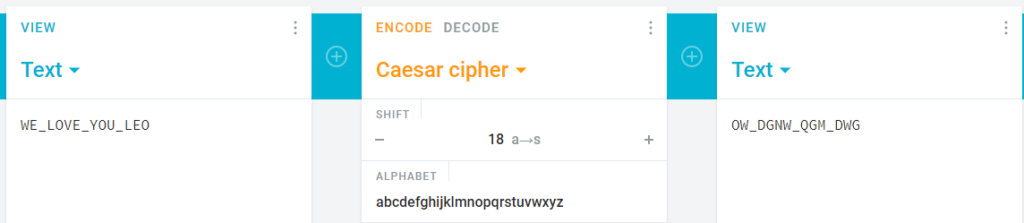
In this challenge we are provided with a encrypted message which we have to decode. The encrypted message was a Caesar Cipher. I just decrypted it with 18 shifts.
This is Very simple : [ 50 ]
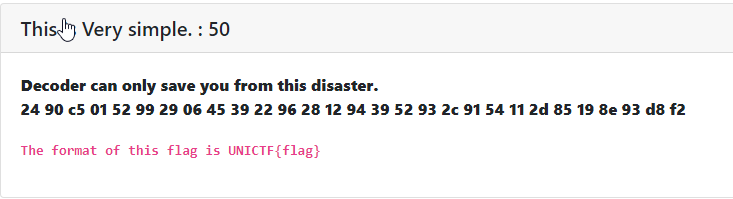
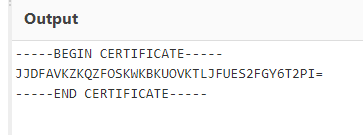
In this challenge we are provided with a hexadecimal number. This was a tricky challenge. First I had to decode it to PEM & got a base32 data. I decoded it twice & got the flag.
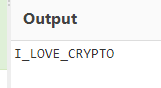
Crypto 004 : [ 100 ]
In this challenge we were provided with a cipher data which was encoded in base64. I just browsed to cyberchef & paste the data. CyberChef automatically detected the base64. From the base64 decoded data I got a png file data. I simply render that & got the flag.

Is cipher always hide the message! : [ 100 ]
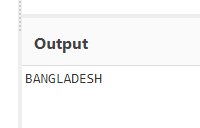
In this challenge we were provided with a encrypted message which was a vigenere cipher. The encrypted message was “DYOKCDUMDS” & the key was “CYBERDRILL”. I just decrypted it & got the flag.
Incident Handling:
Here we were provided with two pcap files & some other files. From these pcap files we have to find flags & answer the questions. The first pcap file was “university_ctf_pcap.pcapng” & the second pcap file was “findtheflag.pcapng”. To analyze the pcap files I used Wireshark.
Prerequisite: To solve these challenges you have to know the basics of networking, what are protocols, how to use Wireshark.
Incident Handling 001 : [ 50 ]
In this challenge we were provided with two file. One is a passwd file & the another one is shadow file. We had to get the password of the user nahid. I just copied the password hash with the username of nahid & used john to decode the password for me.
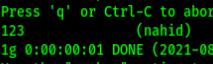
N:B: The question was wrong. The username had to be nahid but was ctf. There was no user named ctf on the file.
Incident Handling 002 : [ 100 ]
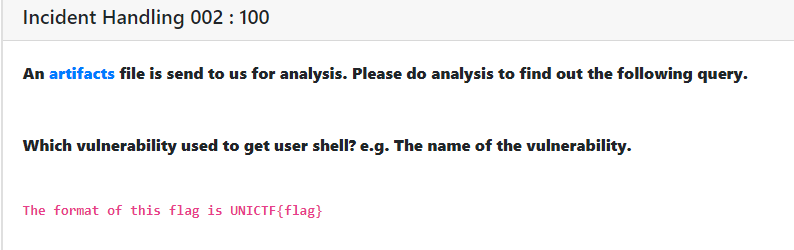
In this challenge we had to find the answer from the first pcap file. In the final flag the vulnerability was mentioned.
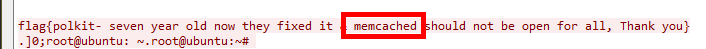
So the flag was UNICTF{memcached}.
Incident Handling 003 : [ 100 ]
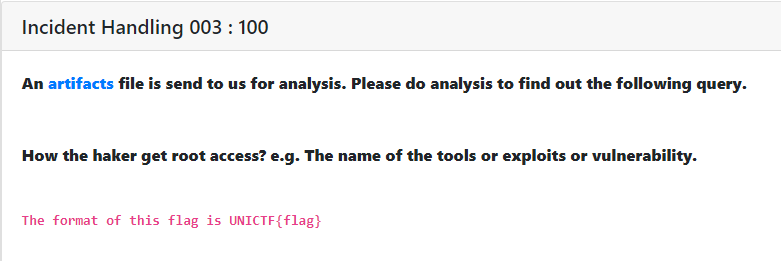
Also in this challenge we had to find the answer from the first pcap file. In the final flag the exploit was mentioned.
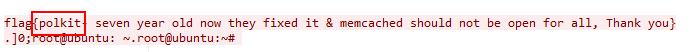
So the flag was UNICTF{polkit}.
Incident Handling 004 : 100
This challenge contained the second pcap file. When I was analyzing the network packets I saw some image file has been captured. So I just exported the HTTP data & analyzed them one by one. There was a png headers & jpg headers in the file. I changed the file extension as per there file header. The jpg image file contained the flag.

Incident Handling 005 : [ 100 ]
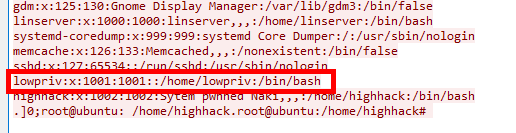
In this challenge we had to find the answer from the first pcap file. I checked the TCP stream from the last. After checking some stream I got the low privilege username.
Incident Handling 006 : [ 100 ]
Also in this challenge we had to find the answer from the first pcap file. This challenge also contained the same pcap file. I checked the TCP stream form the last. In the second last TCP stream I got the main flag.
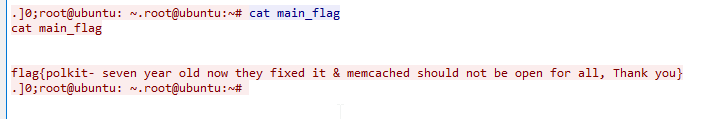
That’s it. Hope you guys enjoyed. Don’t forget to share your feedbacks in the comment section below and stay tuned with us for more interesting challenge walkthroughs.



xoss