Hello Everyone!
I’m Tareq from Knight Squad
Recently we’ve played a CTF. And this is a writeup for a Forensics challenge named “Zstegosaurus”.
In this challenge we are provided with some txt and a png file. As we have a image file we can do various operations like checking the image header, running binwalk, exiftool, pngcheck, steghide, zsteg etc. Since the challenge name is “Zstegosaurus” we can run zsteg to get details about the image file.
After running zteg on the image file we can see lsb & msb data. In the lsb text value we can see the flag.
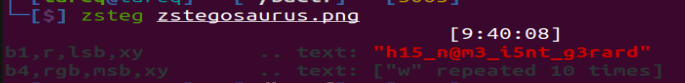
So that was the flag. Hope you guys enjoyed. It was really a very easy challenge. Don’t forget to share your feedbacks in the comment section below and stay tuned with us for more interesting challenge walkthroughs.
Thank You
tareq@knightsquad


