Assalamualikum. I’m Tareq! This is a writeup for Forensics – FlagHunt 2022 Finals. Let
Version:
In this challenge, we are given a memory dump file & we have to find out the os name from the file. We are going to use volatility 3 for analyzing the memory dump. Let’s run the windows.info command in volatility to get the os information.
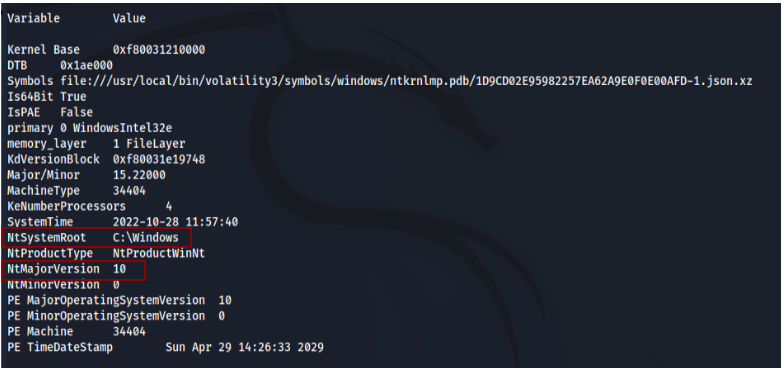
Here we can see the system root is windows & the version is 10.
So the flag of the challenge is: CTF_BD{windows_10}
PRID:
In this challenge, we have to find out the process ID of firefox. But the flag was the Parent Process ID. The question should be asked for PPID. Using pslist command in volatility we’ll get the PID’s of every process of the dump file. Just need to find out the parent process ID of firefox.
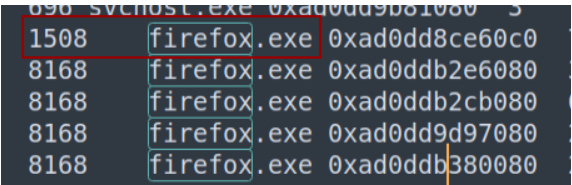
Here you can see the parent process ID is 1508. So the flag is: CTF_BD{1508}
RLog:
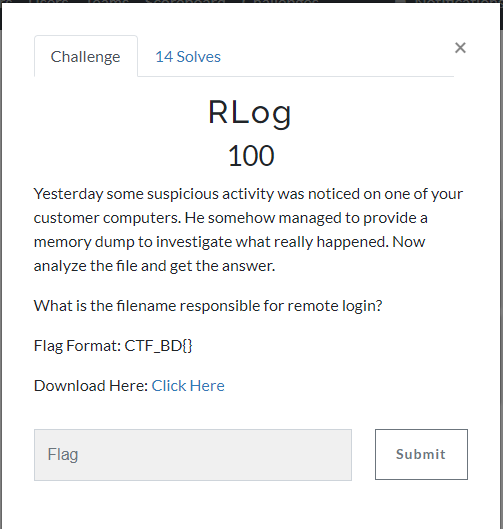
If we analyze the processes, we can see that there is an executable name rdpclip.exe which is responsible for remote login.
So the flag is: CTF_BD{rdpclip.exe}
NContent:
In this challenge, we have to extract the data written in notepad. So we are going to dump the notepad process using memdump command in volatility.
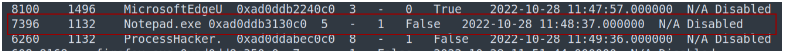
Here we can see the process id of the notepad is 7396. Now let’s dump the memory from this process.
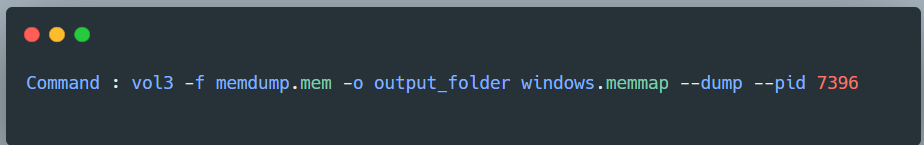
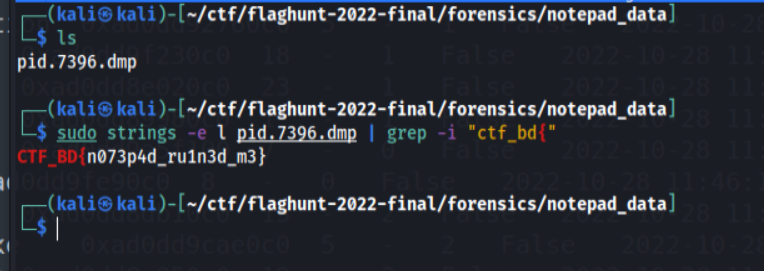
As you can see there is a dump file. Now let’s use the strings command & get the flag.
So the flag is: CTF_BD{n073p4d_ru1n3d_m3}
WWT:
In this challenge, we have to find out the time when the winlogon.exe was executed for the first time.
Using the pslist command we can get the executed time of all the processes. In the above picture, we can see the executed time of winlogon.exe.
So the flag is: CTF_BD{2022-10-28_11:43:54}
Newbie hacker 0x0:
In this challenge, we are asked to find out the number of unique SSID’s. Open the file in Wireshark & navigate to the wifi tab. Count the SSID’s exclude the duplicates.
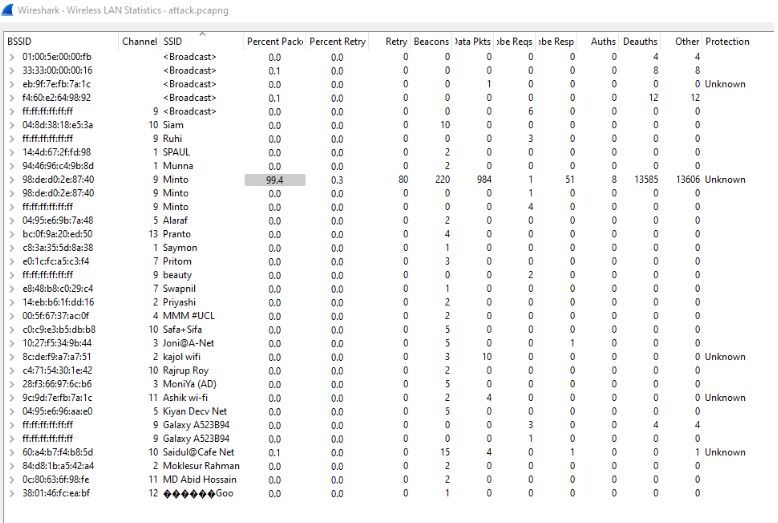
The number will be 25. So the flag is: CTF_BD{25}
Newbie hacker 0x1:
In this challenge, we are given a pcap file. Now we need to analyze it & find out what kind of attack was performed. So let’s analyze the file.
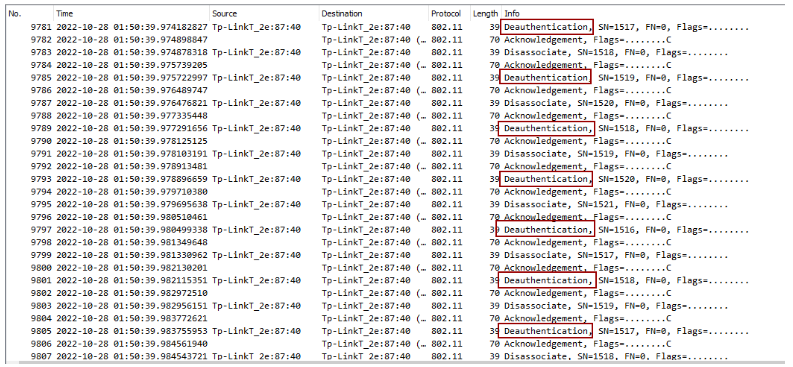
Analyzing the pcap, we can see that someone was trying to hack wifi using deauthentication attack. So the flag is: CTF_BD{deauthentication}
Newbie hacker 0x2:
In this challenge, we are asked to find out the victim’s SSID. As we know that someone was trying to hack the wifi. So there are two possible things that can happen. The hacker might successfully hack the wifi or not. So let’s analyze the file & see if the hacker was able to hack the wifi or not. We will use https://apackets.com/ this site to analyze the pcap.
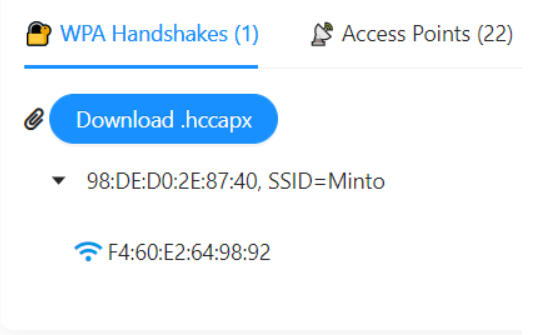
Here we can see there is a password hash file for Minto. So it means the hacker was able to hack Minto’s wifi network. So the flag is: CTF_BD{Minto}
Newbie hacker 0x3:
In this challenge, we have to find out the mac address of Saidul@CafeNet. I uploaded the pcap file to a website name https://apackets.com/ . After analyzing the access points I got the mac address.
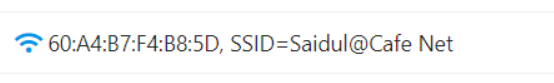
So the flag is: CTF_BD{60:A4:B7:F4:B8:5D}
Newbie hacker 0x4:
In this challenge, we have to find the password from the file. For this, I used aircrack-ng to retrieve the password.
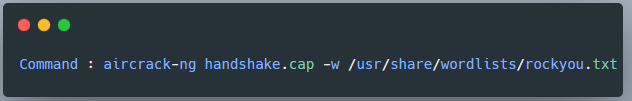
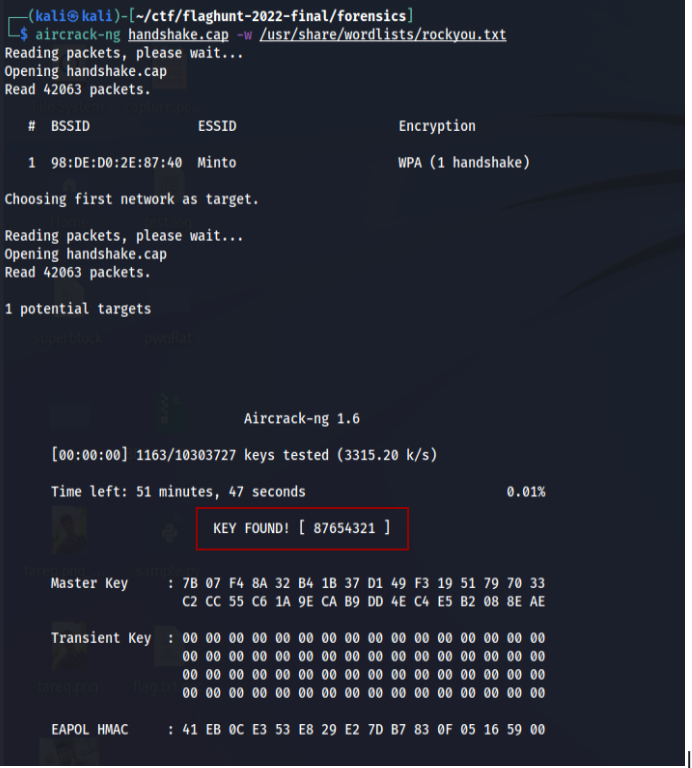
And that’s how I got the key. So the flag is: CTF_BD{87654321}
Thanks 😀


