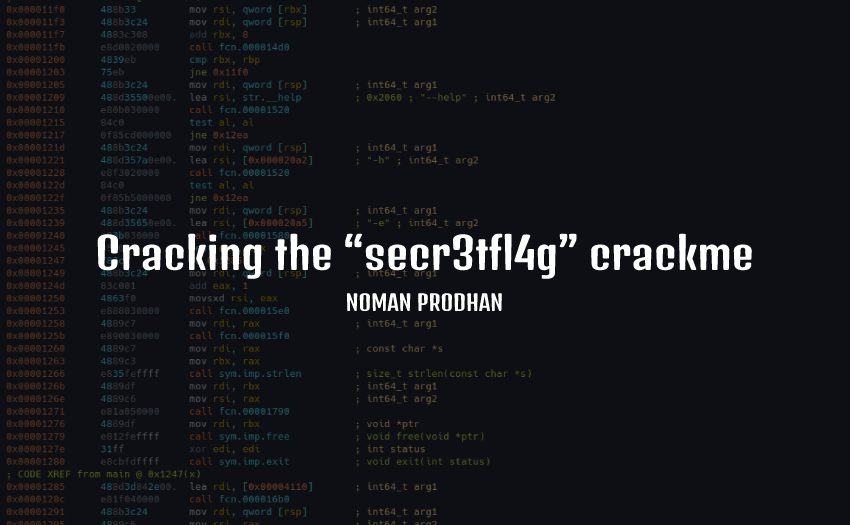
Hey crackers,
Today I am going to crack “secr3tfl4g” crackme from Crackmes.one. You can download the binary from here.
This is a simple crackme and we need to find the right flag. However, let’s start cracking…
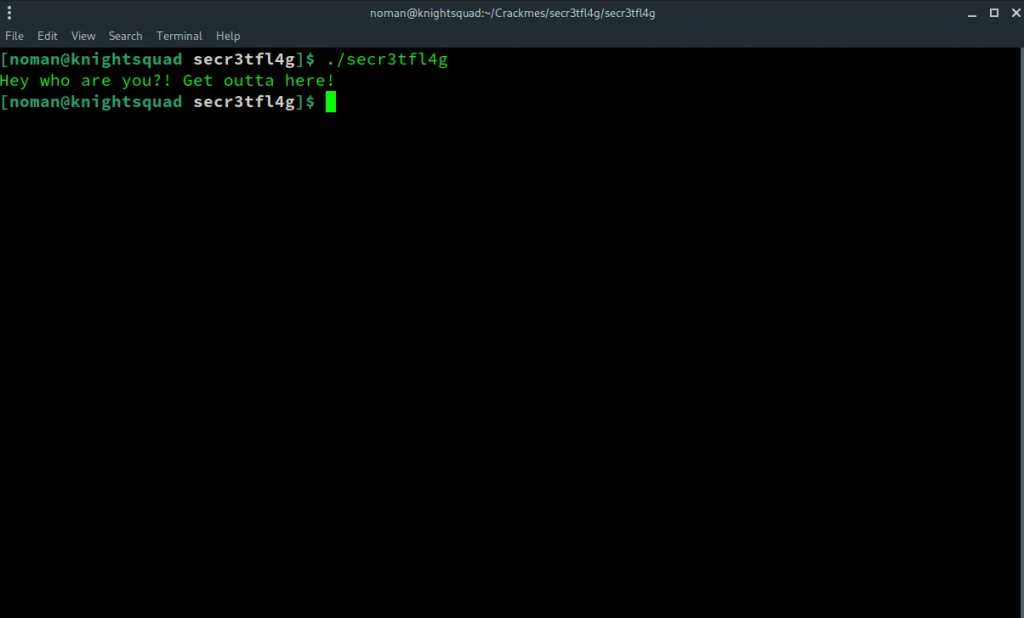
First I tried running the binary and it showed that I was missing the libssl.so.1.1 library from my system. Since I am using Manjaro Linux (Arch based distro), I used pacman to install the openssl-1.1 package. Now I ran the binary without any problem and got the following output
Now, time to reverse it… I opened the binary with Radare2 and started analyzing it and it seems that the binary has multiple functions. But I’m interested in the “main” function because the C program starts executing from it.
First the program checks if we have specified at least 1 argument to it.
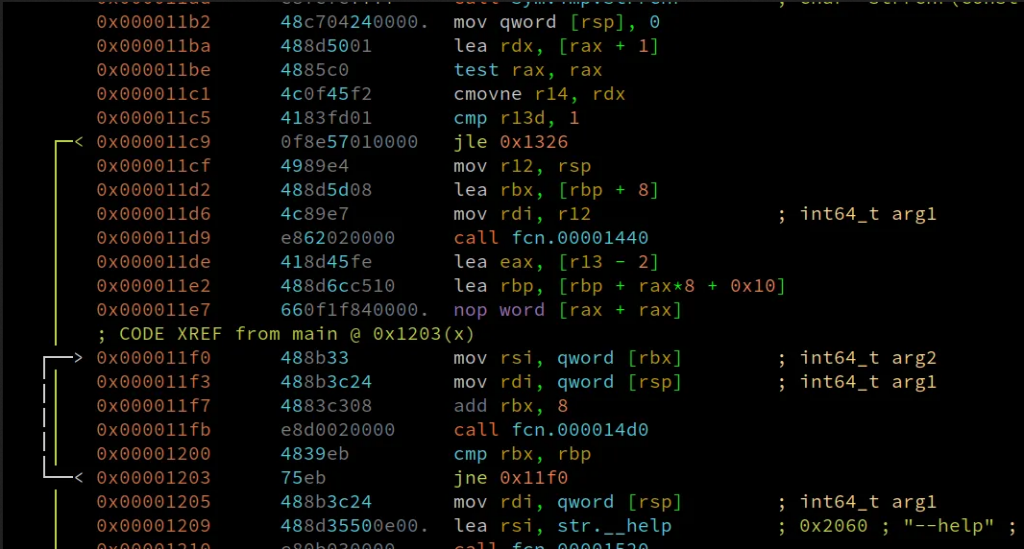
After further analysis, I found out that the binary is checking if we specify the following options..
--help : This displays the help document
-h : This displays the help document
-e : It encrypts/encode the second argumentI am not interested in these arguments, I just want the flag. So I started debugging the program. It seems that the first few conditions are to check if we have used any of the three arguments or options. I set a few breakpoints and one of them was at 0x563cc34ed29f which was giving a jump to the error message “Hey who are you?! Get out of here!”.
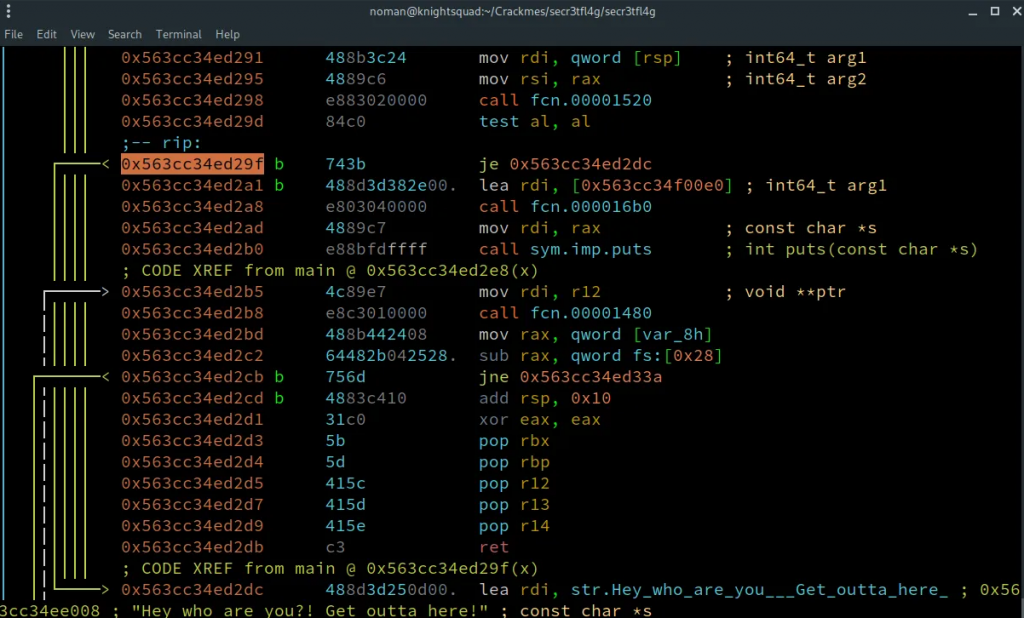
So, I set the RIP value in the next instruction (0x557ad9dae2a1) and continued the program…. BOOM I got the flag
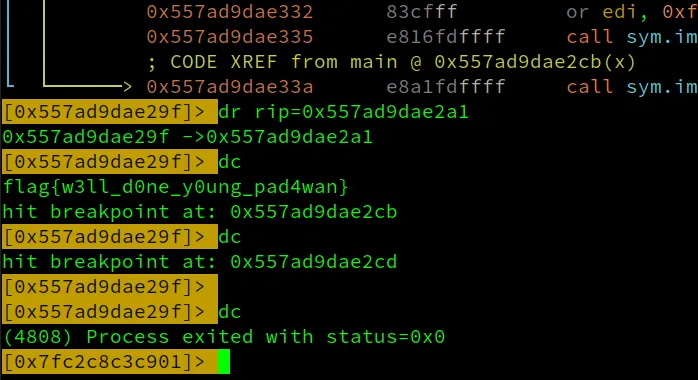
After getting the flag I wondered if there was an easier way to get the flag 🤔
So I started again … 🙃
I ran the binary with ltrace and found something interesting..
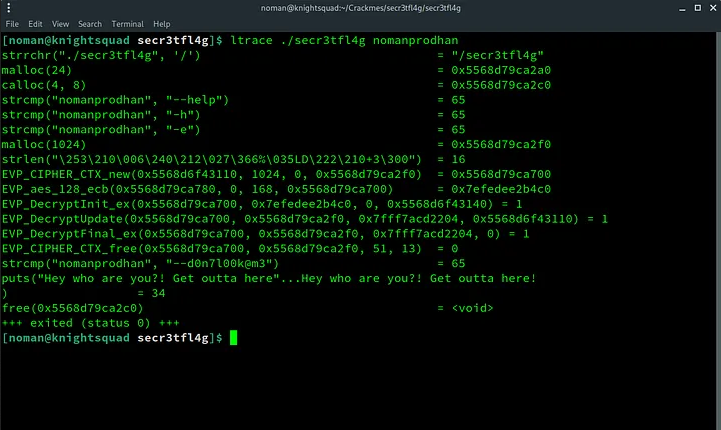
So, it is comparing our input with the following…
--d0n7l00k@m3I passed that as an argument and BOOM.. I got the flag again
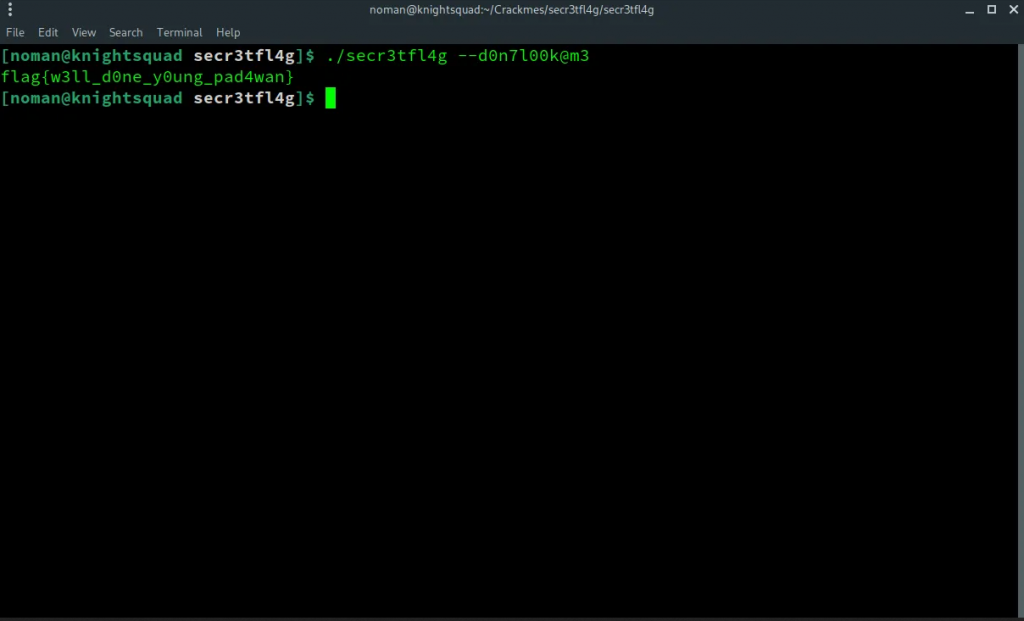
So, we can get flag in both ways and I think there can be more ways to get flag. However, let me know if you got the flag in another way.
Happy Hacking 🤟