Hello! I’m Tareq from Knight Squad.
Recently National Cyber Drill 2021 was held & total 396 teams participated. Challenges were sorted by challenge category.
Here I’m going to give you a quick writeup for the challenges that I was able to solve. I Hope you guys will find this helpful. You will find all the challenges here : http://13.92.58.29/CyberDrill/NCD-2021/ [ Thanks to Abrar Mostafiz YEALID ]
===================== Basic =====================
Eagles eye shot!! : 25
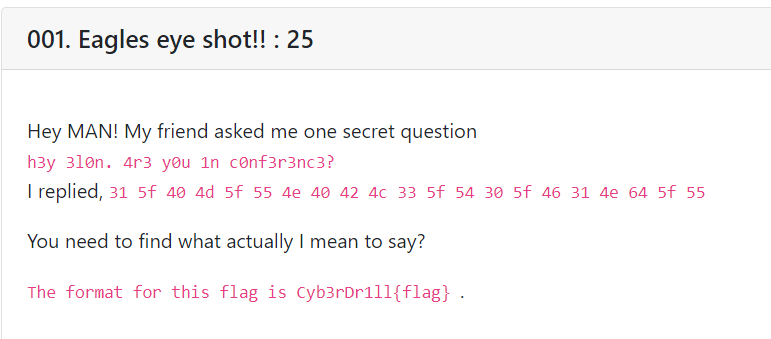
In this challenge we have to find out the actual message of Elon. There’s a hex value in reply. Just decode it from hex & you’ll get the flag.
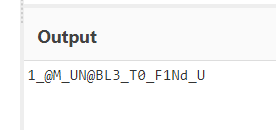
Flag : Cyb3rDr1ll{1_@M_UN@BL3_T0_F1Nd_U}
Warmup : 50
In this challenge we are provided with a txt file. The txt file contains base64 encoded text. Keep decoding the base64 until you find meaningful text.
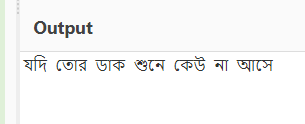
Flag : Cyb3RDr1ll{যদি তোর ডাক শুনে কেউ না আসে}
MR. VEGENERE : 50
In this challenge we are provided with a cipher text with a key. The challenge title mentions VEGENERE. It’s clearly ensures that it’s a vegenere cipher. Let’s just decode it. The cipher text is “COEPOCFNMGM” & key is “BGD e-GOV CIRT” as the vegenere key can only contain letters the right key is “BGDeGOVCIRT”. The decoded text is : BIBLIOKLEPT
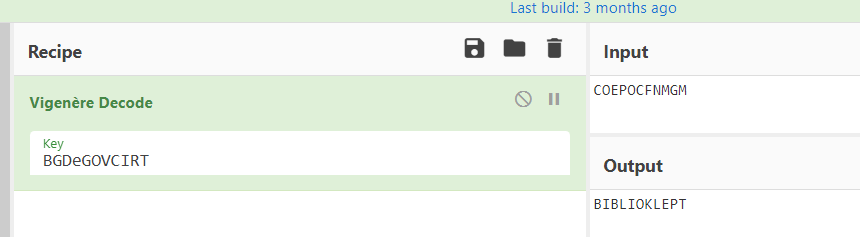
Flag : Cyb3RDr1ll{BIBLIOKLEPT}
ZIPPED : 100
In this challenge we are provided with a zip file which contains 99 zip files. We have to write a script to unzip the files.
Bash Script :
for a in {1..99}; do for z in *.zip; do unzip $z; rm $z;done;doneAfter this we will get a png file which contains the flag.
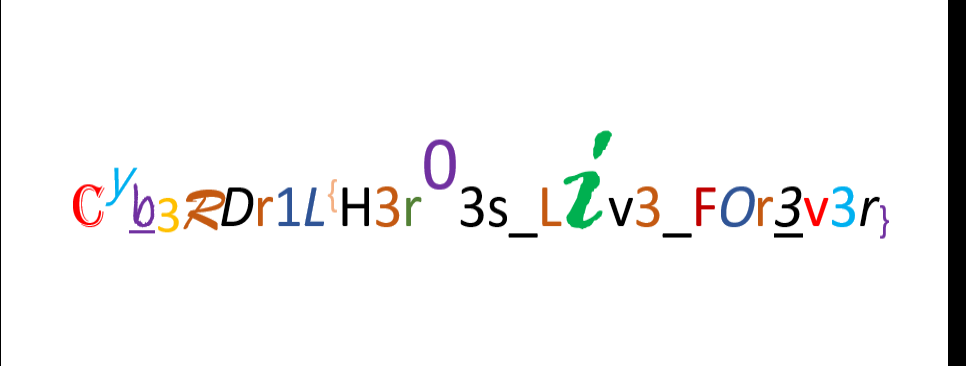
Flag : Cyb3RDr1L{H3r03s_Liv3_F0r3v3r}
===================== Network ===================
In the Network category we are provided with a pcap file which we have to analyze & answer the questions.
Name might be always blank!!! : 25:
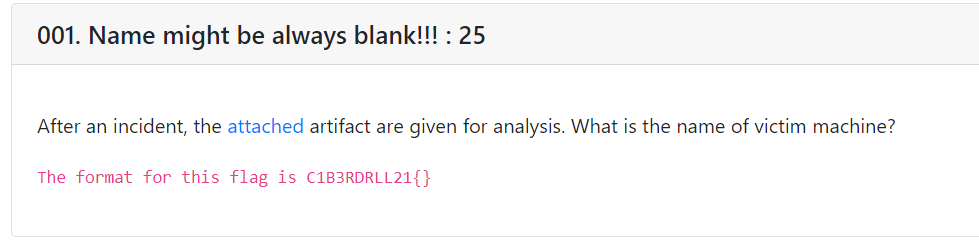
In this challenge we have to find the machine name of the victim. If we just run strings command on the pcap file we will get the machine name.
Command:
strings NCD-2021.pcap | less
or
strings NCD-2021.pcap | grep -i "Desktop"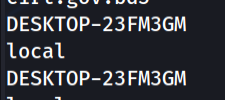
Flag : C1B3RDRLL21{DESKTOP-23FM3GM}
V1CTmi53 : 25
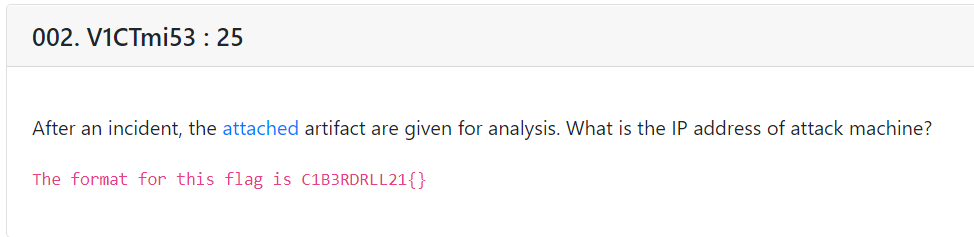
In this challenge we have to find the IP address of attack machine..
If we analyze the pcap file, we can see the attacker used ftp service to get into the victim’s machine. So the source IP is the attacker IP.
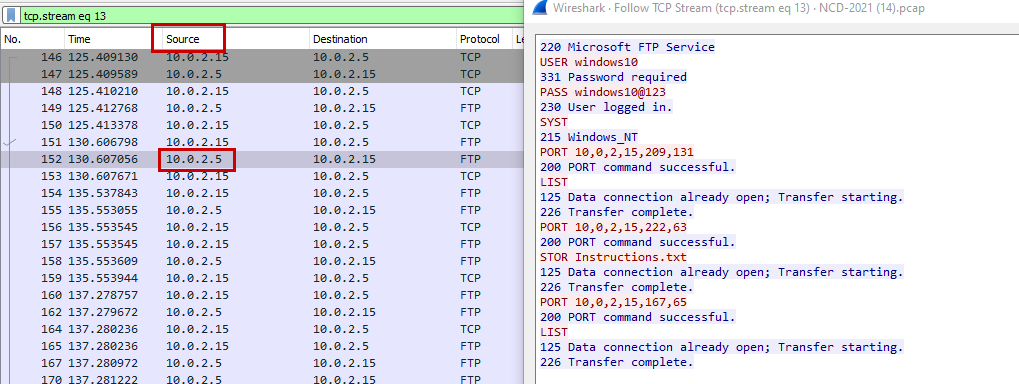
Flag: C1B3RDRLL21{10.0.2.15}
Newbie : 25
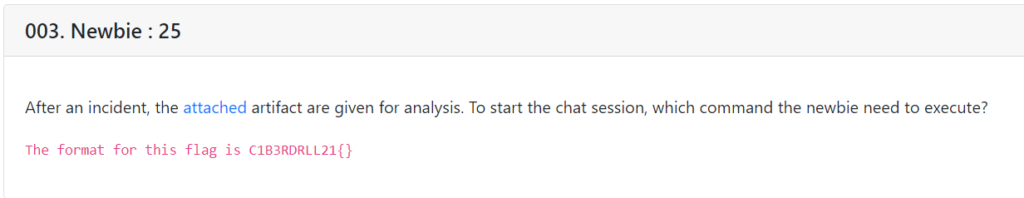
In this challenge we have to find which command the newbie need to execute to start the chat session. If we analyze the pcap file or extract all the HTTP traffic from the pcap file & save them all, we can see a png file is being tranferd through the network. If we open that png file we can see a command & an instruction. The instructions says to change the port number. So here we are sure that we have the command, we just have to change the port number. If we analyze the packet, we can see the Destination Port & the Source port. The “Destination” port was the desire port number. So the command is nc64.exe -lvp 443 & that’s our flag.
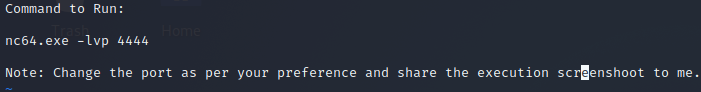
Flag : C1B3RDRLL21{nc64.exe -lvp 443}
Rythmic cords! : 25
In this challenge we have to find the port number of the chat session. Analyzing the packets we can see some text is being transferred. We can consider them as the chat session. The “Destination” port number was the desire port number.
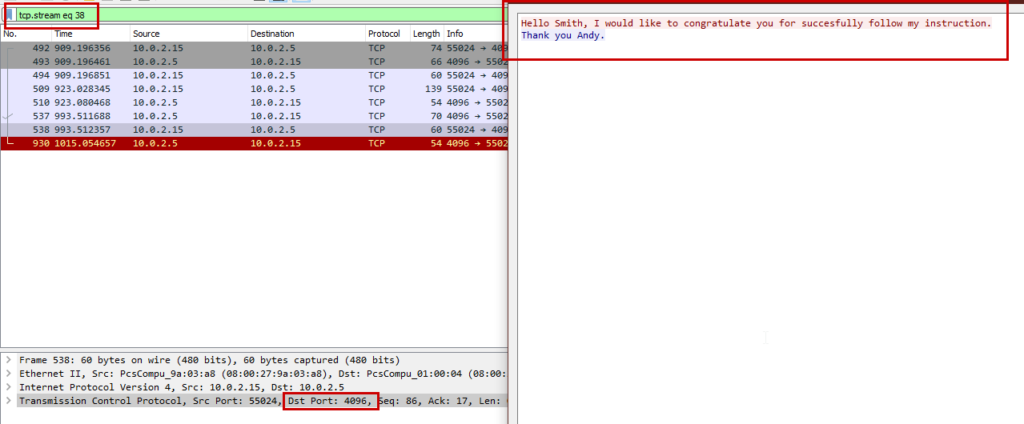
Flag : C1B3RDRLL21{4096}
When your friends betray you, sometimes the only people you can trust are strangers. : 25
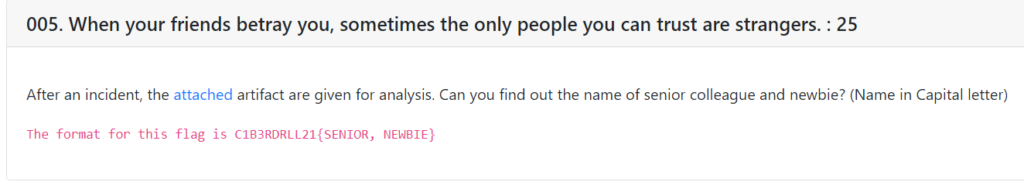
In this challenge we have to find out the name of senior colleague and newbie. Analyzing through the packets, we can see some chats between two persons. Red & Andy. As Andy was guiding Red, Andy is the senior collogue.
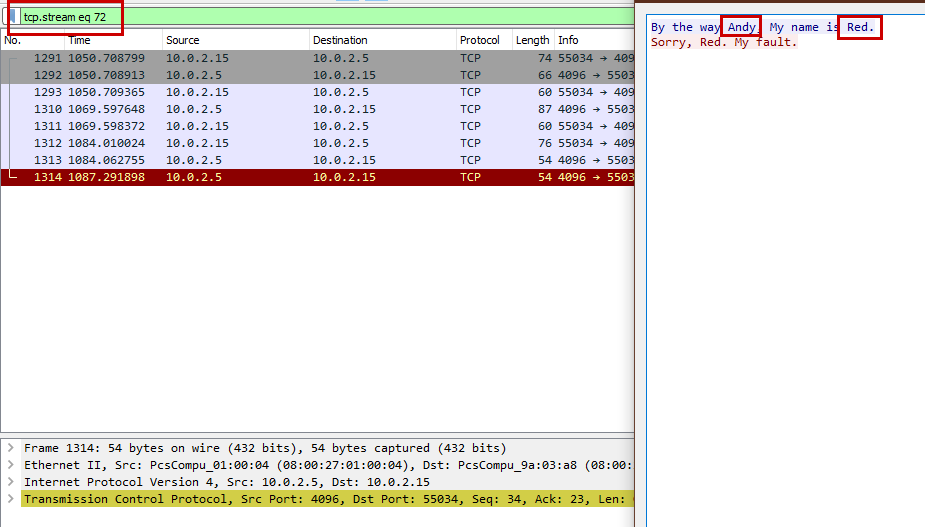
Flag : C1B3RDRLL21{ANDY, RED} (Name in Capital letter)
500 internal server error : 25
In this challenge we have to find out the service used by the attacker to connect to the victim machine. As I mentioned before, the attacker used FTP service to access the victim machine. So the answer is ftp. [ lowercase ]
Flag : C1B3RDRLL21{ftp}
Do you know the hashcat always says meow? : 25
In this challenge we have to find a log file in the packets. If we analyze the packets, we can see so file in ftp. There’s also a log file name JBKFIUCTL5CEKQ2SLFIFISKPJZPUWRKZ.log. At first I thought this was the flag. But it wasn’t. The filename is base32 encoded. Decoding the text from base64, we will get our desire file name.
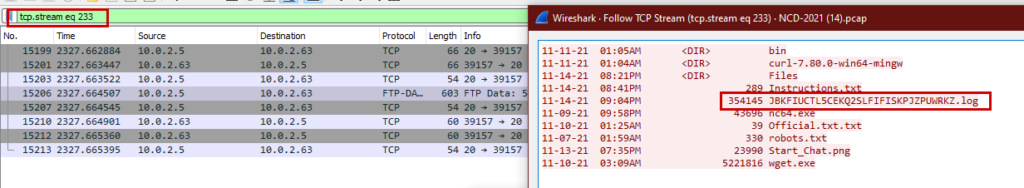
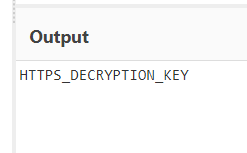
Flag : C1B3RDRLL21{HTTPS_DECRYPTION_KEY}
CHAOS 3: Scientists are continuously trying to invent something. : 100
In this challenge, we have to find out the tool name used by the attacker to get the ftp credentials of the target machine. Analyzing the packets, we can see a .QR_C0d3.png file. It seems like the qr code image might be interesting. After decoding the qr code we get the ftp credentials. But the questions asked for the tool name. After more analyzing the packets I found a .deb file in the GET requests. “zbar-tools_0.23.92-4_amd64.deb“. This was the tool name.
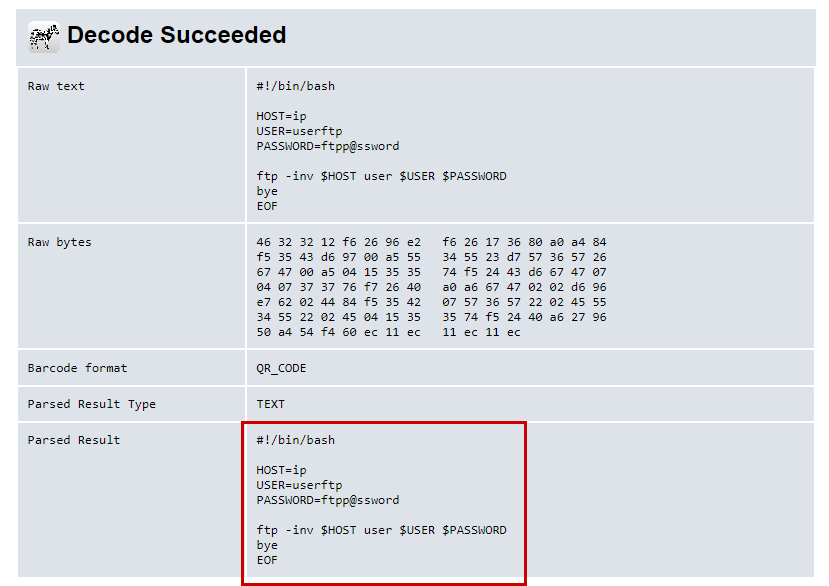
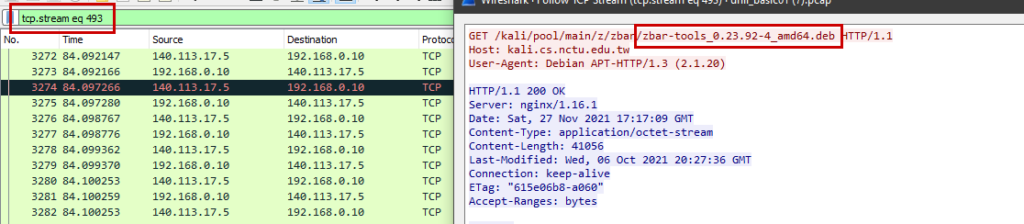
Flag : NCD21{zbar-tools} [ Suggestion : If you don’t know about the zbar tools, Google it ]
===================== Web ===================
CHALLENGE 1: LOCAL STORAGE : 50
In this challenge we are given with a webpage from where we have to find the flag. As the challenge title mention’s Local Storage & descriptions says “Search for flag in local storage!”, we can check the local storage in our dev tools to see if something interesting there.
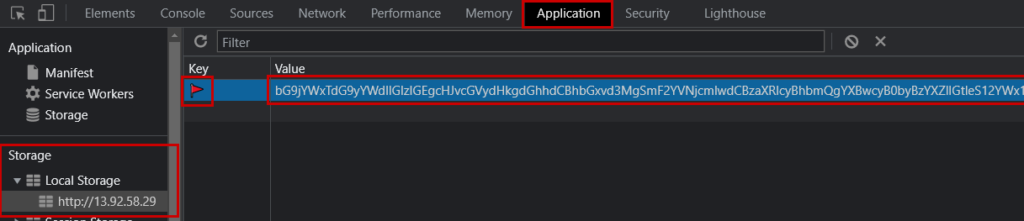
Yes. In the local storage there’s a base64 encoded text. Just decode it & you’ll get the flag.
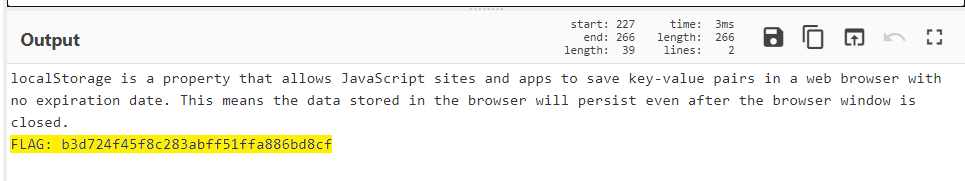
FLAG: cyb3RDr1ll{b3d724f45f8c283abff51ffa886bd8cf}
CHALLENGE 2 : UNPACK JAVASCRIPT : 50
In this challenge we are provided with a webpage. As the challenge title says, Unpack JavaScript, it means we have to do something with JavaScript.

If we see the source code, we can see a lot of JavaScript codes. At the end of the file we can see a comment that says, “Decode this JS file to get 🚩”. In the comment we are given a JavaScript code with encoded eval function which is not really understandable by newbies. Let’s decode the js. I am going to use [ https://lelinhtinh.github.io/de4js/ ] this site. After decoding the eval we get our flag.

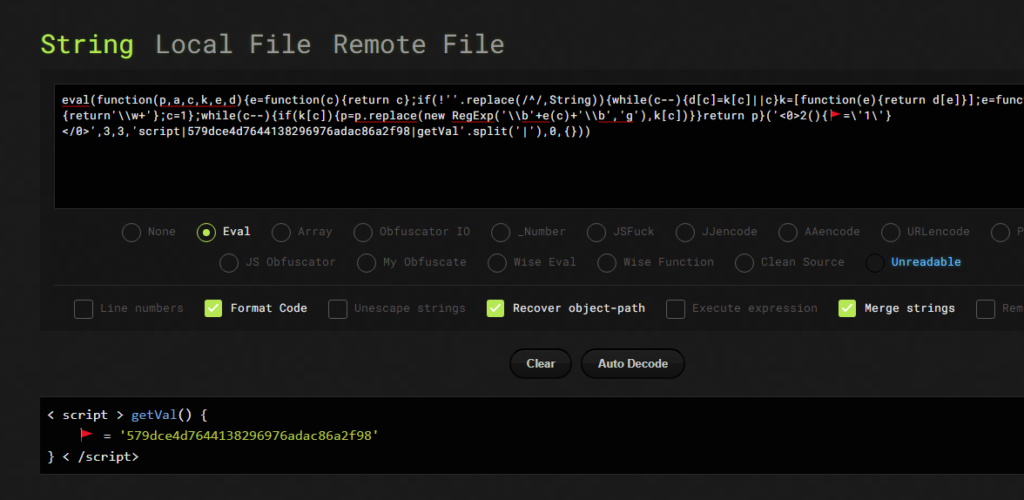
Flag : cyb3RDr1ll{579dce4d7644138296976adac86a2f98}
CHALLENGE 3: DECODE PHP : 50
In this challenge we have to decode a strings which is a php script. The strings is provided in the web page. If we just take the encoded string & paste it to cyberchef you’ll automatically get the flag.
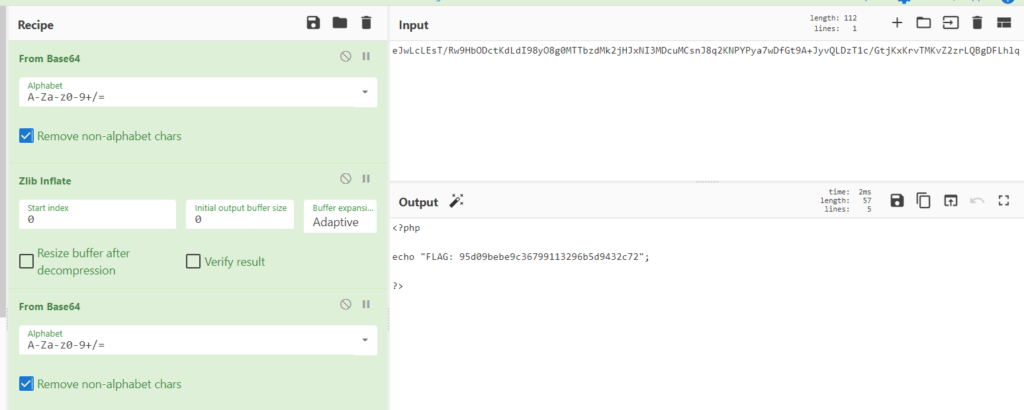
FLAG: cyb3RDr1ll{95d09bebe9c36799113296b5d9432c72}
CHALLENGE 4: DECODE JS : 100
In this challenge we have to decode an encoded string. The webpage provides us the encoded string file location. Going to that location, we can see a lot of special characters. It is JJencode. So let’s just decode the strings with JJencode decoder & get our flag.
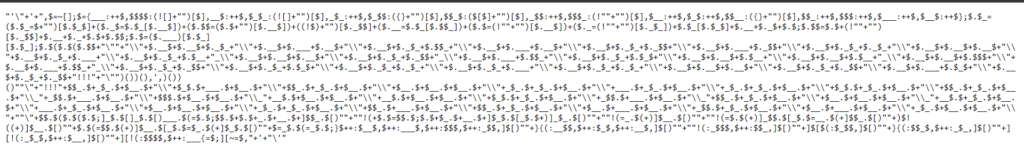
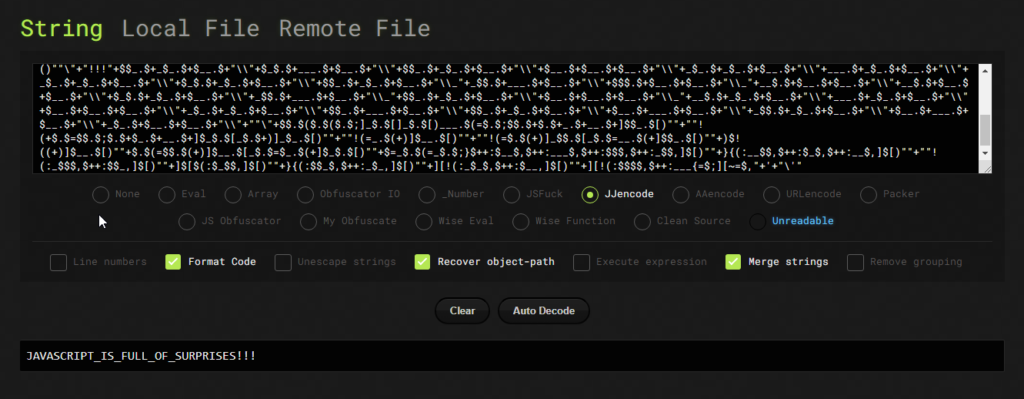
Flag : cyb3RDr1ll{JAVASCRIPT_IS_FULL_OF_SURPRISES!!!}
CHALLENGE 5: SYMBOLS CAN DO THE MAGIC : 100
In this challenge again we are provided with an encoded string. The webpage provides us the encoded string file location. Going to that location, we can see a lot of special characters. It is JSFuck. So let’s just decode the strings with JSFuck decoder & get our flag.

Flag : cyb3RDr1ll{WRITE_AND_EXECUTE_CODE_BY_USING_ONLY_SIX_CHARACTERS!}
That’s it. I hope you’ll find this blog really helpful. Don’t forget to share your feedbacks in the comment section below and stay tuned with us for more interesting challenge walkthroughs.


